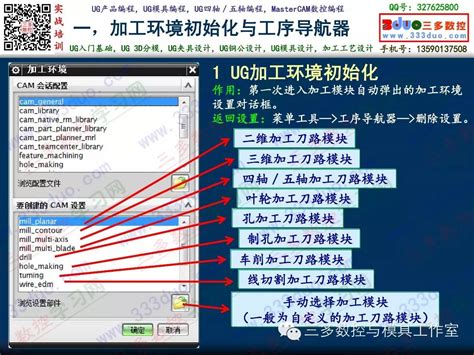
您所在的位置:首页 - 热点 - 正文热点
编程里面是什么意思
![]() 春浙
2024-05-05
【热点】
403人已围观
春浙
2024-05-05
【热点】
403人已围观
摘要**Title:UnderstandingClaimsinProgramming**Intherealmofprogramming,a"claim"typicallyreferstotheactofa
Title: Understanding Claims in Programming
In the realm of programming, a "claim" typically refers to the act of asserting ownership or exclusive access to a particular resource, whether it's a variable, a file, or a section of memory. Claims play a crucial role in ensuring the integrity and security of software systems, particularly in multithreaded or distributed environments where multiple entities may compete for the same resources. Let's delve deeper into the concept of claims in programming, their significance, and best practices associated with handling them effectively.
The Concept of Claims
In programming, a claim is a statement or declaration made by a component of a system regarding its right to access or manipulate a resource. This resource could be anything from a piece of data in memory to a network connection or a hardware device.
Example:
In a multithreaded application, multiple threads may attempt to access a shared variable concurrently. To prevent data corruption or race conditions, each thread must "claim" exclusive access to the variable before performing any operations on it. This is typically done using synchronization primitives such as locks or semaphores.
Significance of Claims
Claims serve several important purposes in software development:
1.
Resource Management:
Claims help manage access to shared resources, preventing conflicts and ensuring that only authorized entities can modify or use them.2.
Concurrency Control:
In concurrent programming, claims are essential for coordinating access to resources among multiple threads or processes, thus avoiding data inconsistencies and race conditions.3.
Security:
Claims play a vital role in enforcing security policies within a system. By requiring entities to prove their entitlement to access certain resources, claimsbased security mechanisms help prevent unauthorized access and protect sensitive data.Types of Claims
Claims can be categorized based on various criteria, including their scope, duration, and granularity. Some common types of claims include:
1.
Mutex Claims:
Used for providing exclusive access to shared resources among multiple threads or processes. Mutexes ensure that only one entity can hold the claim to a resource at any given time, thereby preventing concurrent access.2.
Ownership Claims:
Denote exclusive ownership of a particular resource by a specific entity. Ownership claims are typically used in resource management scenarios where a resource must be released or cleaned up once its owner no longer requires it.3.
Access Control Claims:
Govern access to resources based on the permissions or privileges granted to individual entities. Access control claims are prevalent in securitysensitive applications where certain operations or data should only be accessible to authorized users or processes.
Best Practices for Handling Claims
To effectively manage claims and ensure the robustness of software systems, developers should adhere to the following best practices:
1.
Acquire Claims Atomically:
When claiming a resource, ensure that the operation is performed atomically to avoid race conditions and inconsistencies. Use synchronization primitives such as mutexes or atomic operations to achieve atomicity.2.
Release Claims Promptly:
Once a resource is no longer needed, release the claim to allow other entities to access it. Failing to release claims promptly can lead to resource leaks and potential deadlock situations.3.
Avoid Overlapping Claims:
Be mindful of the scope and duration of claims to prevent overlapping or conflicting access to resources. Clearly define ownership and access control policies to minimize contention and maximize resource utilization.4.
Implement FineGrained Claims:
Wherever possible, use finegrained claims to minimize contention and improve concurrency. Instead of claiming entire data structures or resources, consider partitioning them into smaller units that can be claimed independently.5.
Enforce Security Policies:
In securitycritical applications, leverage claimsbased security mechanisms to enforce access control policies rigorously. Authenticate and authorize entities based on their claims, and restrict access to sensitive resources accordingly.Conclusion
Claims play a fundamental role in programming, enabling developers to manage resource access, control concurrency, and enforce security policies effectively. By understanding the concept of claims and adhering to best practices for handling them, developers can build robust, scalable, and secure software systems that meet the demands of modern computing environments.
Tags: 爱死亡和机器人第二季 十字军之王2 谁让我当红 时间计算器 网游排行榜
版权声明: 免责声明:本网站部分内容由用户自行上传,若侵犯了您的权益,请联系我们处理,谢谢!联系QQ:2760375052
最近发表
- 特朗普回应普京涉乌言论,强硬立场引发争议与担忧
- 民营企业如何向新而行——探索创新发展的路径与实践
- 联合国秘书长视角下的普京提议,深度解析与理解
- 广东茂名发生地震,一次轻微震动带来的启示与思考
- 刀郎演唱会外,上千歌迷的守候与共鸣
- 东北夫妻开店遭遇刁难?当地回应来了
- 特朗普惊人言论,为夺取格陵兰岛,美国不排除动用武力
- 超级食物在中国,掀起健康热潮
- 父爱无声胜有声,监控摄像头背后的温情呼唤
- 泥坑中的拥抱,一次意外的冒险之旅
- 成品油需求变天,市场趋势下的新机遇与挑战
- 警惕儿童健康隐患,10岁女孩因高烧去世背后的警示
- 提振消费,新举措助力消费复苏
- 蒙牛净利润暴跌98%的背后原因及未来展望
- 揭秘缅甸强震背后的真相,并非意外事件
- 揭秘失踪的清华毕业生罗生门背后的悲剧真相
- 冷空气终于要走了,春天的脚步近了
- 李乃文的神奇之笔,与和伟的奇妙转变
- 妹妹发现植物人哥哥离世后的崩溃大哭,生命的脆弱与情感的冲击
- 云南曲靖市会泽县发生4.4级地震,深入了解与应对之道
- 缅甸政府部门大楼倒塌事件,多名官员伤亡,揭示背后的故事
- 多方合力寻找失踪的十二岁少女,七天生死大搜寻
- S妈情绪崩溃,小S拒绝好友聚会背后的故事
- 缅甸遭遇地震,灾难之下的人间故事与影响深度解析
- 缅甸地震与瑞丽市中心高楼砖石坠落事件揭秘
- 揭秘ASP集中营,技术成长的摇篮与挑战
- 徐彬,整场高位压迫对海港形成巨大压力——战术分析与实践洞察
- ThreadX操作系统,轻量、高效与未来的嵌入式开发新选择
- 王钰栋脚踝被踩事件回应,伤势并不严重,一切都在恢复中
- 刘亦菲,粉色花瓣裙美神降临
- 三星W2018与G9298,高端翻盖手机的对比分析
- 多哈世乒赛器材,赛场内外的热议焦点
- K2两厢车,小巧灵活的城市出行神器,适合你的生活吗?
- 国家市监局将审查李嘉诚港口交易,聚焦市场关注焦点
- 提升知识水平的趣味之旅
- 清明五一档电影市场繁荣,多部影片争相上映,你期待哪一部?
- 美联储再次面临痛苦抉择,权衡通胀与经济恢复
- 家庭千万别买投影仪——真相大揭秘!
- 文物当上网红后,年轻人的创意与传承之道
- 手机解除Root的最简单方法,安全、快速、易操作
- 缅甸地震与汶川地震,能量的震撼与对比
- 2011款奥迪A8,豪华与科技的完美结合
- 广州惊艳亮相,可折叠电动垂直起降飞行器革新城市交通方式
- 比亚迪F3最低报价解析,性价比之选的购车指南
- 商业健康保险药品征求意见,行业内外视角与实用建议
- 官方动态解读,最低工资标准的合理调整
- 东风标致5008最新报价出炉,性价比杀手来了!
- 大陆配偶在台湾遭遇限期离台风波,各界发声背后的故事与影响
- 奔驰C级2022新款,豪华与科技的完美融合
- 大摩小摩去年四季度对A股的投资热潮